How Quantum Computing is breaking Cryptography and Redefining Cybersecurity
Quantum computing is no longer just science fiction.
It’s real, it’s advancing fast, and it’s set to change the way we think about technology.
With incredible processing power, quantum machines promise to solve complex problems that classical computers can’t touch.
That’s exciting—but also a little alarming.
Why?
Because the same power that unlocks new possibilities could also break the encryption we rely on every day.
From banking apps to medical records, our digital world depends on cryptography to stay safe.
🔐 Understanding Cryptography and Cybersecurity
Cryptography is the art of securing information by converting it into unreadable formats, ensuring only authorized parties can access it.
At its core are keys, used to encrypt and decrypt data.
Symmetric Keys: One key is shared for both encryption and decryption, making it fast but requiring secure sharing of the key.
Asymmetric Keys: Uses two keys—a public key for encryption and a private key for decryption. This is more secure, as the private key is never shared.
In cybersecurity, cryptography plays a crucial role in protecting sensitive data, ensuring secure communications, and verifying identities.
Understanding these concepts is essential as threats evolve in our increasingly connected world.
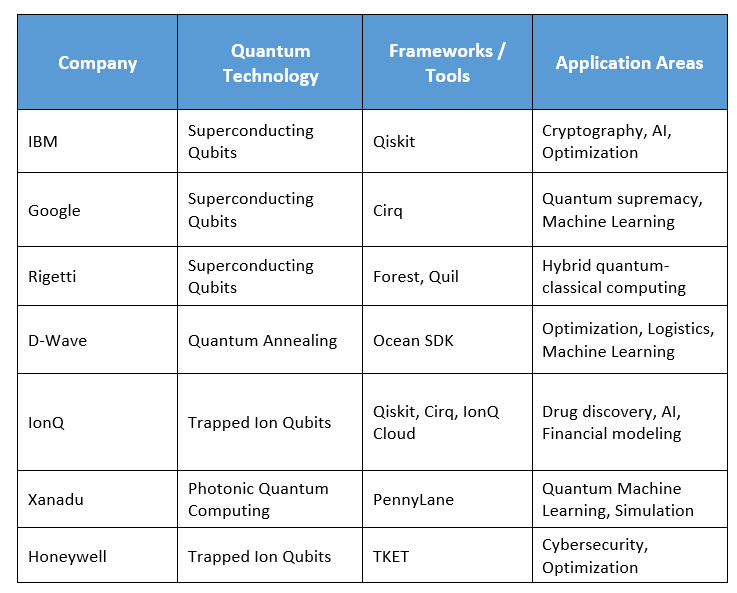
🏛️ Companies Researching Quantum Computers
Explanation of Key Elements:
Quantum Technology: The type of qubits used, e.g., superconducting, trapped ions, or annealing.
Coding Frameworks/Tools: The programming platforms or SDKs companies provide for developers to build quantum applications.
Applications: Real-world problems being addressed with the company’s quantum solutions.
🛡️ Quantum Threat to Cryptography
Modern cryptography relies heavily on mathematical problems that are computationally difficult for classical computers to solve.
Algorithms like RSA, ECC and DSA are built on the assumption that tasks such as factoring large integers or solving discrete logarithms are practically infeasible with existing computational power.
But quantum computing changes everything.
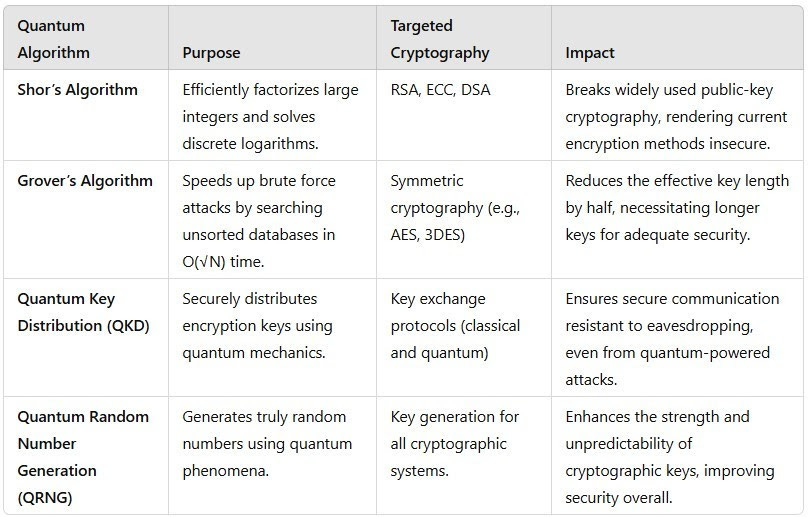
✅ Shor’s Algorithm
This quantum algorithm can efficiently factor large integers, breaking RSA and ECC encryption. A strong RSA-2048 key, secure today, could be cracked in hours by a powerful quantum computer.
✅ Grover’s Algorithm
Symmetric systems like AES are more resistant, but Grover’s Algorithm speeds up brute-force attacks. AES-256 would offer the same protection as AES-128 in a quantum world—meaning key sizes must double to stay secure.
📊 Implications for Cybersecurity
The ability of quantum computers to break classical cryptographic systems has profound implications for cybersecurity, impacting everything from personal privacy to national security.
Here's what you need to know:
1. Vulnerability of Current Systems
Critical infrastructure such as finance, healthcare, and government relies on classical encryption. Quantum attacks could expose sensitive data like bank info or classified records.
2. Retrospective Attacks
Adversaries may store encrypted data now and decrypt it later with quantum power. This threatens long-term privacy of files, trade secrets, and more.
3. Post-Quantum Cryptography
To stay ahead, experts are developing quantum-resistant algorithms. NIST is leading efforts to standardize new methods like lattice-based and hash-based cryptography.
As the quantum era approaches, businesses and governments must act now to secure their systems and prepare for the future. The stakes couldn’t be higher!
🎲 Opportunities for Cybersecurity
While quantum computing poses significant risks, it also offers powerful tools for enhancing cybersecurity. Here’s how quantum advancements can revolutionize the field:
1. Quantum Key Distribution (QKD)
QKD uses principles of quantum mechanics, such as entanglement and the no-cloning theorem, to enable secure communication.
Any attempt to intercept quantum-encrypted data disrupts the quantum state, alerting the parties involved and ensuring the security of the transmission.
2. Quantum Random Number Generation (QRNG)
The unpredictability of quantum mechanics can be harnessed to generate truly random numbers, which are critical for secure cryptographic keys.
QRNG could significantly improve the strength of encryption systems, adding an extra layer of protection to sensitive data.
3. Advanced Threat Detection
Quantum computing can process massive amounts of data in real time, enabling faster and more accurate detection of cyber threats.
This could revolutionize how organizations monitor and respond to attacks, ensuring a more proactive approach to cybersecurity.
⚡ Quantum Algorithms and Their Impact
📅 Preparing for a Quantum Future
The timeline for practical quantum computers capable of breaking encryption remains uncertain, ranging from a decade to several decades.
However, the cybersecurity community must act now to ensure readiness:
Transition to Quantum-Resistant Algorithms: Organizations should begin transitioning to post-quantum cryptography to protect their systems.
Education and Awareness: Governments, businesses, and individuals must be educated about the risks and opportunities posed by quantum computing.
Research and Collaboration: Continued investment in quantum research and partnerships will be essential to stay ahead of emerging threats.
⚖️ Conclusion
Quantum computing is a double-edged sword, offering transformative possibilities while threatening to upend modern cryptographic systems.
As we stand on the brink of this technological revolution, the cybersecurity community must balance its risks and opportunities.
By proactively embracing quantum-resistant technologies and leveraging the power of quantum mechanics for defense, we can ensure a secure digital future in an era dominated by quantum computing.